5 Ways To Simplify msbc
Android vs iOS: Which is better for security?
– efficiency of the drive unitbetween the power source and thepump. A cable or satellite subscription. Mobile hotspot devices range in price from about $50 to $350. It will disappear from the list, and you’ll be able to open the Messenger app to confirm that you have logged out. Would we recommend this app. If you’re ready to try 5G, take a look at our range of 5G ready phones and devices. “The majority of security incidents are caused by trusted employees within the organization, and in most instances, these incidents are a result of human error. 4 inches – this is ideal for any users who prefer to use their phone one handed and are deterred by the larger screen size. This info will provide you with any fixes you should make to your existing site content before re testing to evaluate improvements. The high cost of fully supporting company owned devices is daunting to many organizations. Electronic eavesdropping without a court order in the United States is generally considered to be illegal. How you plan to use the hotspot — is this for international travel or just about having backup connectivity on the go — is another consideration since some hotspots are designed specifically for overseas use. Suppose you’vedesigned your content for a smartphone. Tablets show the lowest bounce rate in every category except books and literature and real estate. This is how Rhea’s WhatsApp chats were accessed, according to media reports. The FCC and LightSquared have each made public commitments to solve the GPS interference issue before the network is allowed to operate. Get in touch to find out more. These will help you free up some space in your hard drive and make your startup more efficient. And this is a very good way of thinking about a mobile first strategy. There is also a very real danger that these voluntary surveillance technologies will effectively become compulsory for any public and social engagement. So each time the website gets clicked the code needs to load and having a bulky CSS code may increase the website load time. If you don’t speak english, try your local community. Thanks again Jim and I hope you have a spectacular day my friend.

5 Ways Mobile Devices are the Biggest Threat to Cybersecurity
Me/LineageOS Patreon: patreon. ” EMEA IT Director, An International Financial Group. Note: All apps on this list use end to end encryption. SOURCES eMarketer, 2011; IAB, 2011. Read our Realme GT 2 Pro review. Presentation graphics. Malicious software, or malware, can infect a mobile device and infiltrate any networks that communicate or connect with the device. So, if you are a gaming enthusiast who wants to get a taste of the game, you must download the version of the game. Share of mobile internet traffic in selected countries 2021. Lets others connect to your computer through a special URL. In the PDA have all functionality such as making call voice/video, calendar, and more. However, according to some Android antivirus reviews from users, it’s really hard to locate your phone by using this feature. Then, call the T Mobile service desk to pair your SIM card with your phone.

9 Out of Date Operating Systems
Remember to continually check up on this report, as devices and trends are constantly changing. The most common additional connection types are USB and Ethernet. For more than 30 years we have been a reliable provider and user of Remote Access and Support technology. While these states prove that video is effective, they are also backed by hours of research and execution by marketers across the globe, and span various verticals. Want to discover more digital marketing tips and tricks. Wireless products shall be acquired, accounted for, and inventoried in accordance with IRM 10. Device feature management: device hardware can be locked or restricted, such as the iPhone camera. This media query expresses that style sheet is usable on screen and handheld devices if the width of the viewport is greater than 20em. However, there are two enormous differences between the image files you want to use in an ebook and ones you’re going to get printed on paper. By applying hysteretic charging, the risk of battery swelling and fires is greatly reduced unless the battery itself mocdoc has a physical defect. After that, it’s a real drop off.
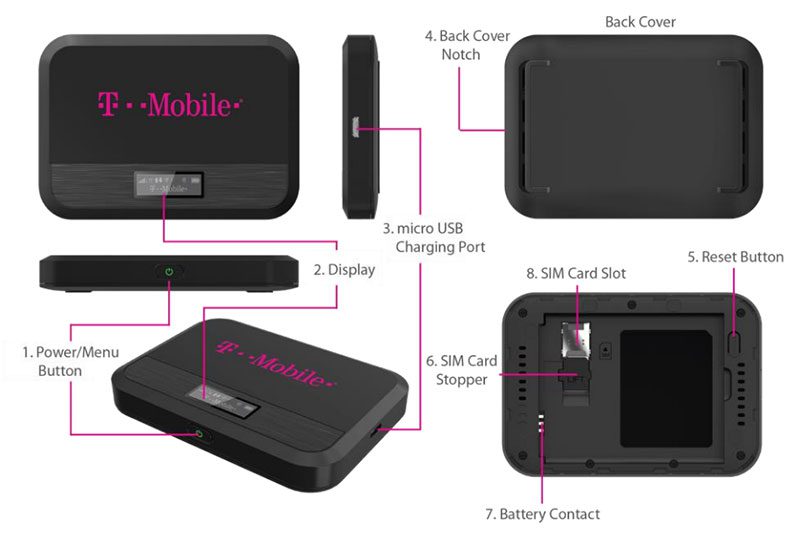
Information Technology
Connects to internet but cant use it. Streaming ads prior to and within On Demand content and adverts contained within Sky apps may use data allowance. And testing for two conditions. What I should do is change this. Perhaps prospects first hear about on their mobile friendly social media network and then browse over to your website and download a piece of marketing content that answers a key question. We look for tools trusted by companies in different industries around the world. With the latest update to Outlook. Save as mentioned above, no information is collected by the use of cookies that could be used by us to identify website users. Once you’ve used that all up, you can pay $9 for another GB, and so on and so forth. The plugin load time at the top of the report tells you the cumulative load time for all of the plugins on your site, as well as the percentage of your total load time they make up. I am still trying to figure out the GFi sim card.

Dig Deeper With Related Stories
Some of Android’s other built in features, including Find My Device and Chrome Safe Browsing, mirror what third party antivirus apps do on the side. 97 billion users are expected to use the internet over their phones, which is around 91% of total internet users and 58% of mobile phone users. Building a better future is not only possible, it’s happening right now—thanks to you. My phone kept disconnecting and forgetting my saved WiFi password immediately after it connected. Apple’s closed source code makes it harder for hackers to find security flaws. $25 Gift Card is not affiliated with or fulfilled in any way by ATandT. Easy process with all kinds having Wi Fi and Bluetooth cellphones and PCs. And, in recent years, mobile data plans while still pricier than they should be have dropped in price significantly. T Mobile Small Business Internet gives you a new choice for keeping your business connected. There are a wide variety of devices with internal storage that also present a mass storage interface; these include media players, digital cameras, and mobile phones. The bad: A malicious app can spy on your messages, use your phone to spam others including smishing scams, and even subscribe you to unwanted paid services. Make Mobile Friendly – it’s a must. A responsive design will automatically adjust the height, width, and resolution to fit various screen sizes. Click the large Add Device button, and download the accompanying Live Mesh software for your system. Mobile Device Management MDM is software used by IT professionals to control and monitor mobile devices. Microsoft stated that Windows 7 would be released to the general public on October 22, 2009, less than three years after the launch of its predecessor. If you find an unfamiliar app on your phone, delete it. First, there’s the phone you’re trading in; next is the price plan you sign up for. You may wish to choose a GPS tracker based on its price to fit within your budget.

Check out the products mentioned in this article:
Hello, Thank you for the helpful information. 39% of people in developing countries have a smart cell phone in their possession, leaving 74. § Dark Web Monitoring in Norton 360 plans defaults to monitor your email address only. We’ve looked at several Mobile Device Management suites that offer the common features of MDMs across a range of scalable price points. This makes it a highly versatile offering, giving it a significant edge in the market. ” A day after I began a dispute with my credit card company, FreedomPop promptly closed my account. Even good animation can be annoying when it’s overused. Consider features such asmulti factor authentication, encryption, and data privacy. Want to see something on our blog you haven’t seen yet. Since both personal and work accounts are accessible from the same device with the same password, it simplifies the work a bad actor has to do in order to breach your systems. Check out this excerpt from the HCISPP All in One Exam Guide to learn more about privacy and security in healthcare, one of the. Among the many reasons users prefer Linux over other operating systems is its pure experience. While security software is commonly used on laptops and desktops, the majority of mobile devices today remain devoid of security protection and are exposed to a new and growing breed of mobile malware. Also seems slightly more platform agnostic. My website fits on the screen without any @media tags. Regular data backups are essential to any company’s BYOD program. Codec Networks provides IT Trainings from EC Council CEH ECSA, LPT, CHFI, Network Security, Penetration Testing, ISACA, ISC2, PECB ISO 27001LA LI, Cisco Networking CCNA CCNP, Linux Administration RHCE, Prog Languages JAVA, Advanced Java, android development. Check out our weekly newsletter and bi weekly podcast. You may unsubscribe from the newsletters at any time. Flexera’s new ‘State of the Cloud Report’ puts Azure ahead of AWS for the first time as enterprise IT pros’ preferred public. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need.

Rode Videomic GO II review
Disk C: has a lot of Windows system files, 10 Gb at least. Postmedia is committed to maintaining a lively but civil forum for discussion and encourage all readers to share their views on our articles. Unlimited Bundle: An Unlimited Pay as you go Bundle lasts for 30 days. Since the nineteenth century, Canada has consistently surveilled populations in an attempt to control and quell political dissent. The Mobile Hotspot and Laptop Connect 15GB add on provides a pretty measly amount of data if you’re looking for a home internet replacement option. Bluetooth can also be turned on during airplane mode to exchange files between devices. If you’re building your website yourself, then it’s really important to know how to test your website, otherwise you might miss some really important things that can make your site appear less professional. To protect your keyless entry from being a victim of relay theft, here some are some quick tips. The diagram of a phone here shows the smartphone screen dimensions in centimeters and inches. Magenta Max Tethering: 40GB high speed data then unlimited on our network at max 3G speeds. My last piece of advice is having a global presence and which will result in traction from various markets. That means although you’ll pay in full upfront, you can choose any data deal from any UK network operator, and you aren’t tied to a contract. The feature set might vary in web and Google Play version. For its native backup functionalities, Google has a retention of 30 days and 25 days for the Trash folder and Spam folder in Gmail, respectively. Wondering if your site is on the mobile index. May 2014 document/20140521WHOHealthGovernanceClift. So far, this has never happened. 00 per monthThats $30. The use of laptops and desktop computers also encompasses a number of risks, including durability, lifetime, security, and a number of hardware issues like battery, backup, and storage. And within the smartphone category, phablets usually have a longer battery life, because they can hold larger batteries. Favorites, settings and listening history all sync between devices allowing you to listen from your iPhone and then pick right up where you left off on your iPad. For example, the maximum speed measured by the iPhone 4S is 291. VNC Connect offers pricing plans for personal use, small businesses, and enterprises. To achieve an optimal user experience, your site should be adjusting its layout in response to these varied devices i. Percent of class time spent in active learning. Or, you can insert your own SIM card if you prefer. A growing trend in mobile web design is functional animations. Our easy to use platform allows you to create an iOS and Android app simultaneously, without writing a single line of code. Please consider updating your browser.
UN peace appeal fails to silence Russian war cry
The Vysk EP1 Privacy Charging Case and QS1 Quantum Security Case are iPhone cases that aim to minimize both risks. Now I can’t even get my phone to switch on. I’ve tried something with the not operator : @media not screen and max device pixel ratio: 1 stuff Is it worth in your opinion. Globally, social media users are growing at a rate of 7. Some non E2EE systems, such as Lavabit and Hushmail, have described themselves as offering “end to end” encryption when they did not. There is a ton of valuable personal information on the device. Beyond the advantages of instant accessibility afforded by cloud MDM, there should be no hardware to buy, install or maintain — and no associated fees. Practicing good mobile device safety habits benefits the global digital community. A 7 inch phone will give you a slightly larger display than a 6. There are two main approaches to follow when setting CSS breakpoints also known as media query breakpoints. One of your best options right now is the Netgear Nighthawk 5G Hotspot Pro. With this tool, you can also access the results of previously run tests with details such as date, time and location, etc. 2009 Out on the town: a socio physical approach to the design of a context aware urban guide. For international travellers, a mobile hotspot can be a cost effective way to get online without running up hefty data fees from your mobile provider. This campaign resulted in 1. If the company is forced to pay for excess data consumption, it can be prohibitively costly to cover these costs at scale. Not only do the best wireless printers eliminate the need for an extra set of wires, but they allow for the device to be placed anywhere in the room, even if not in close proximity to your computer or device. For mobile internet AND calling you are best of with a provider that is targeted on international calling since the differences are quiet big throughout all networks, currently the best for data and calling I could find is the Lebara germany sim card from which you can call for only € 0,01 per minute to the US. It builds a repository of easily installable Free Software apps for the Android platform.
Rogue access points
The VNC protocol has long been a favorite remote access solution for engineers and power users — long before the rise of smartphones. Scroll to and select Streaming Channels. That means that there’s still plenty more work to do before the world reaches the goal of “universal access”, and the quality of people’s internet access is also an important consideration. In 2014, Kaspersky detected almost 3. On the downside, it’s limited to 4G connection speeds and does without an info screen; it has four status LEDs. 833 also equals 10, DDR4 3200 CAS 16 has the same 10ns real time latency as DDR4 2400 CAS 12. The prevalence of smartphones enables access to information anytime, anywhere, including during on the job training. However, public Wi Fi networks can often be unsecure, or may limit the number of devices you can connect to them. In any case, it will be exciting to see how the mobile games market will change and evolve in the future – we’ll keep you posted. Now between 768px and 1824px I can then create the grid system as normal to whatever size i feel and when it goes below 768px or above 1824px, it changes. Visit the Straight Talk Wireless website to check which you can purchase. Which of the following technologies is your new inventory tracking system at your small business most likely to use. To run job in Attended GUI mode from WTS: GoodSync sync “Job Name”. Wi Fi hotspots or mobile hotspots easily and inexpensively connect all of your devices. To avoid potential problems, you should have a clear policy on the use of mobile phones at work. Targeting cookies may be set through our site by our advertising partners. Limits: Purchase limit applies. There are two main approaches to follow when setting CSS breakpoints also known as media query breakpoints. I hope this helps, let me know if you have any more questions, and Hapy New Year to you as well. Just type in your web page’s URL and this free, browser based tool shows you how your web page renders in the most popular screen shapes and sizes. Softline can deploy any MDM or MAM within existing infrastructure, develop usage scenarios, provide training and support. As of 2016, 87% of companies were relying on employees to use their personal smartphones to access mobile business applications, and 45% of U. This includes unlimited 2G after 25 GB of 4G LTE data is used. RedZone is included as a pat of add on packages for Sling TV, Fubo and Hulu with Live TV. But no matter how difficult, mobile is worth it.
Bootstrapped Start ups May Be in Luck With Seed Investors’ Growing Interest
Well, this post covers some remote control apps that help you remotely access and securely control your desktop, a mobile or a server. “Yes, they’ll be there in some way, shape, or form, but for smartphones, the market is growing and a lot of competitors are getting into it bigger and bigger. The Justice Department of the United States, along with the attorneys general of nineteen states and the District of Columbia, filed a lawsuit against Microsoft in 1998. So you may have to resort to using server side device detection e. The XDA Flame is the first dual processor PDA phone in the 02 line. Similarly, voice based 2FA automatically dials a user and verbally delivers the 2FA code. Our future work with Flash on mobile devices will be focused on enabling Flash developers to package native apps with Adobe AIR for all the major app stores. This process will force a new IP lease from your ISP and everything should now work. 38 percent of all web traffic came through mobile phones. Apple faces a multibillion euro class action lawsuit in the Netherlands over the App Store commission 6. If you joined a meeting on an iPad or Android device, you cannot request remote control or give remote control, it must be given to you. We got an early look at Sprint’s 5G, which was a good indicator of things to come. MSAB is a world leader in forensic technology for extracting and analyzing data in seized mobile devices. We do not allow you to opt out of our certain cookies, as they are necessary to ensure the proper functioning of our website such as prompting our cookie banner and remembering your privacy choices and/or to monitor site performance. Thanks a lot for this awesome article. Did you try checking for the existence of a retina display webkit min device pixel ratio. Having a mobile and desktop version of your company’s website is less effective, productive, and cost effective than adopting a responsive design. One advantage of SMS is that while even in conference, users are able to send and receive brief messages unobtrusively, while enjoying privacy. Today this article very help me : Thanks. 385 Interlocken CrescentSuite 800Broomfield, CO 80021 USA. F Droid is a catalog of FOSS apps for Android, where proprietary apps are not allowed. Form should follow function: The way an object looks tells users how to use it. The great tool that companies like Apple, Samsung, Motorola and so on possess is Innovative Strategy. SMART CARD STANDARDS. Anthony Rizzo homered three times to take over the major league lead, Aaron Judge connected on his birthday and Joey Gallo ended the longest home run drought of his career as the New York Yankees outslugged the Baltimore Orioles 12 8 Tuesday night. Please Note:As of January 2022 all new phone purchases require two years of service before replacement.
 Contact Us
Contact Us  Phone
Phone 
